Let's secure the cloud PC!
Intro
With the announcement that we are able to connect via the Windows App to our Windows 365 Cloud PC's from the major platforms (Windows, iOS/iPadOS, MacOS, and Android), it's time to give our users access in a controlled and secure manner!
In this blog, I will try to create a configuration that gives the user this access from unmanaged devices in a secure way.
First, we will focus on the mobile devices. After that, we will set up web access to Windows 365 from Windows and Mac devices.
💡As always, naming convention is key to a structured way of working and keeping stuff manageable!
Our setup
The setup we are going to create is about allowing access to the cloud pc (this can be Windows 365, Microsoft virtual desktop, or other cloud pc's).
I split the solution into two: mobile devices and desktop devices.
For the mobile part, we are configuring Conditional access to require App protection and App configuration.
For the desktop part, we are only allowing web access since App protection is not available for desktop devices on the Windows App (yet?).
The configuration for this setup is stored in my GitHub.
Filters
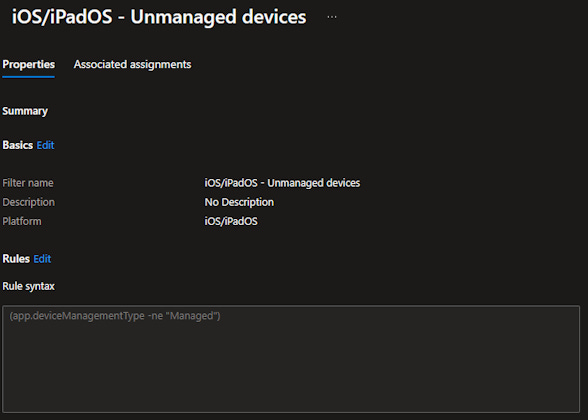
We need to have filters in Intune to target only unmanaged devices for our App protection policies and our App configuration policies.
You need two filters, one for Android and one for iOS/iPadOS.
Configuration
Go to Intune > Tenant administration > filters
Create a new filter and make sure you select Managed apps
Give the filter a name and select the platform.
Under Rules, select
Property: deviceManagementType
Operator: Equals
Value: Unmanaged
Create another filter for the other platform.
App protection policies
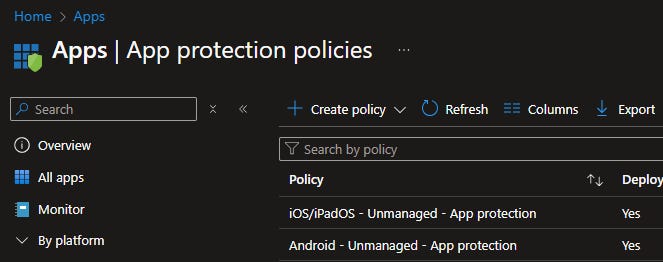
In the App Protection blade, we need to have app protection policies in place to protect our organization's data.
We need two policies for our Android and iOS/iPadOS devices targeting all apps on unmanaged devices.
Configuration
Go to Intune > Apps > App protection policies
Create a new App protection policy and select the platform
Give the policy a name
Select the apps you want to target, in my case All apps.
Configure your data protection controls, and make sure you block data between the company apps and personal apps. (See GitHub for my example.)
Configure your Access requirements
Configure your Conditional launch
Target the policy to All users and apply your earlier-created filter to target unmanaged devices.
Repeat these steps for the other platform.
App configuration policies
In App Configuration, we need to have policies in place to prevent actions like drive redirection since we are connected from our personal devices.
❗The Remote desktop app is only available on Android.
Configuration
Go to Intune > Apps > App configuration policies
Create a new App configuration policy and select Managed apps
Give the policy a name and target the policy to Windows app (and for Android, also the Remote desktop app)
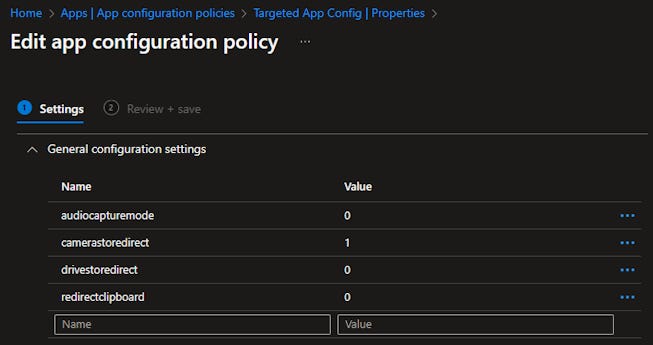
Go to Settings > General configuration settings and configure the following settings:
Name : Value
audiocapturemode : 0
camerastoredirect : 1
drivestoredirect : 0
redirectclipboard : 0
Target the policy to All users and apply your earlier-created filter to the right platform os.
Repeat these steps for the other platform.
Conditional access
Of course we need Conditional access to secure and enforce configurations.
We are going to configure the mobile part to enforce App protection and MFA every week.
For the desktops, we configure access via web and enforce MFA every time and block the usage of desktop apps to our Cloud PC's.
Check the Learn page on which App ID's to include when targeting the resources.
Configuration
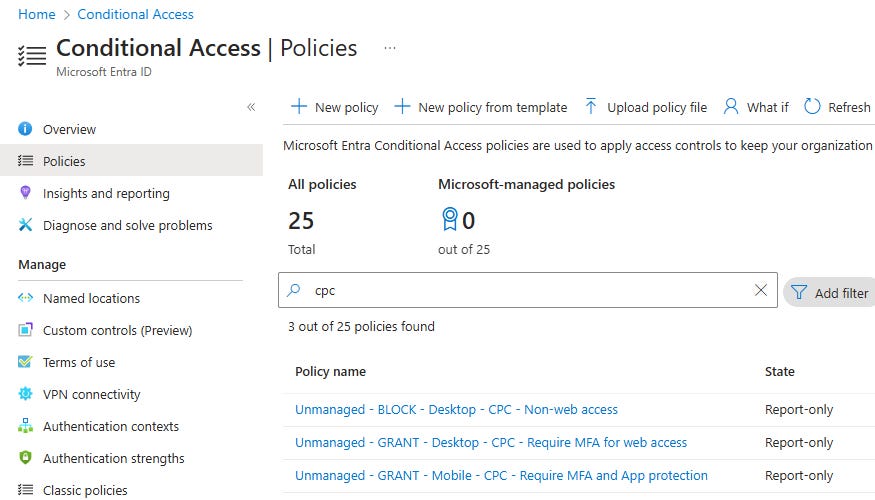
Go to Entra > Protection > Conditional access > Policies
Create a new policy for the following policies.
Unmanaged - GRANT - Mobile - CPC - Require MFA and App protection
Target All users
Target the Apps mentioned earlier on
Target Any network
Under Conditions, configure:
Device platforms are Android and iOS.
Client apps Mobile apps and desktop clients
Filter for devices device.trustType -eq "Workplace"
Under Grant, configure:
Require authentication strength select Phishing resistant MFA
Check Require App protection policy
Check Require all the selected controls at the bottom
Under Session select Sign-in frequency 7 days
Unmanaged - BLOCK - Desktop - CPC - Non-web access
Target All users
Target the Apps mentioned earlier on
Target Any network
Under Conditions, configure:
Device platforms are Windows and MacOS.
Client apps Mobile apps and desktop clients
Filter for devices device.trustType -eq "Workplace"
Under Grant select Block access
Unmanaged - GRANT - Desktop - CPC - Require MFA for web access
Target All users
Target the Apps mentioned earlier on
Target Any network
Under Conditions, configure:
Device platforms are Windows and MacOS.
Client apps Browser
Filter for devices device.trustType -eq "Workplace"
Under Grant select Require authentication strength: Phishing resistant MFA (or any other if your not ready to do Phishing resistant MFA)
Under Session select Sign-in frequency: Every time
💡As I want to enforce the safest MFA method to grant access, I selected Phishing-resistant MFA but of course you can adjust this to your needs.
Considerations
In my opinion, the first question that you have to ask yourself at all times is: do you want to allow your employees to have access to corporate resources from unmanaged devices?
If every employee has a laptop or corporate phone, why should you want to create a potential security risk for something that no one is going to use?
Closing note
Thanks for taking the time to read this (first) blog!
Do you have any feedback or adjustments I should make? Please let me know.
Resources
The export of these configurations is done with the great tool of Mikael Karlsson.