Local admin segmentation with Entra and Intune
Intro
These days, local administrators are becoming less essential thanks to Endpoint Privilege Management (EPM). But practically, we do see that it’s far from gone yet.
This blog has been sitting in draft for a while now, but hey—it's never too late to update and publish, right?
I wondered how everyone keeps control of their environments with the tools available in Microsoft Entra and Microsoft Intune.
In this blog, I'll share my thoughts on how you can bring all the necessary controls together into a cohesive, working solution.
💡 As always, naming convention is key to a structured way of working and keeping stuff manageable!
Our setup
Groups
The groups used in this setup are sometimes linked to multiple controls. To keep track of which groups are used in various configurations, I have used Intune Assistant.
I firmly believe in automating as much as possible, so wherever possible, I use dynamic groups (see GitHub for the dynamic membership rule).
Device groups
Win-Dev-Standarduser
Note: I am aware that the Operator Contains is no longer considered best practice anymore.Win-Dev-Administrator
These groups are dynamically assigned.
This way, a device with no Autopilot tag is, by default, classified as a StandardUser device—supporting a “secure by default” approach.
User groups
Win-Usr-StandardUser
Win-Usr-LocalAdministrator-All
Note: This group is used for Entra users who need to be local admins on all devices.Win-Usr-LocalAdministator
Note: This group is attached to the role Microsoft Entra Joined Device Local Administrator.
These groups are statically assigned.
Entra
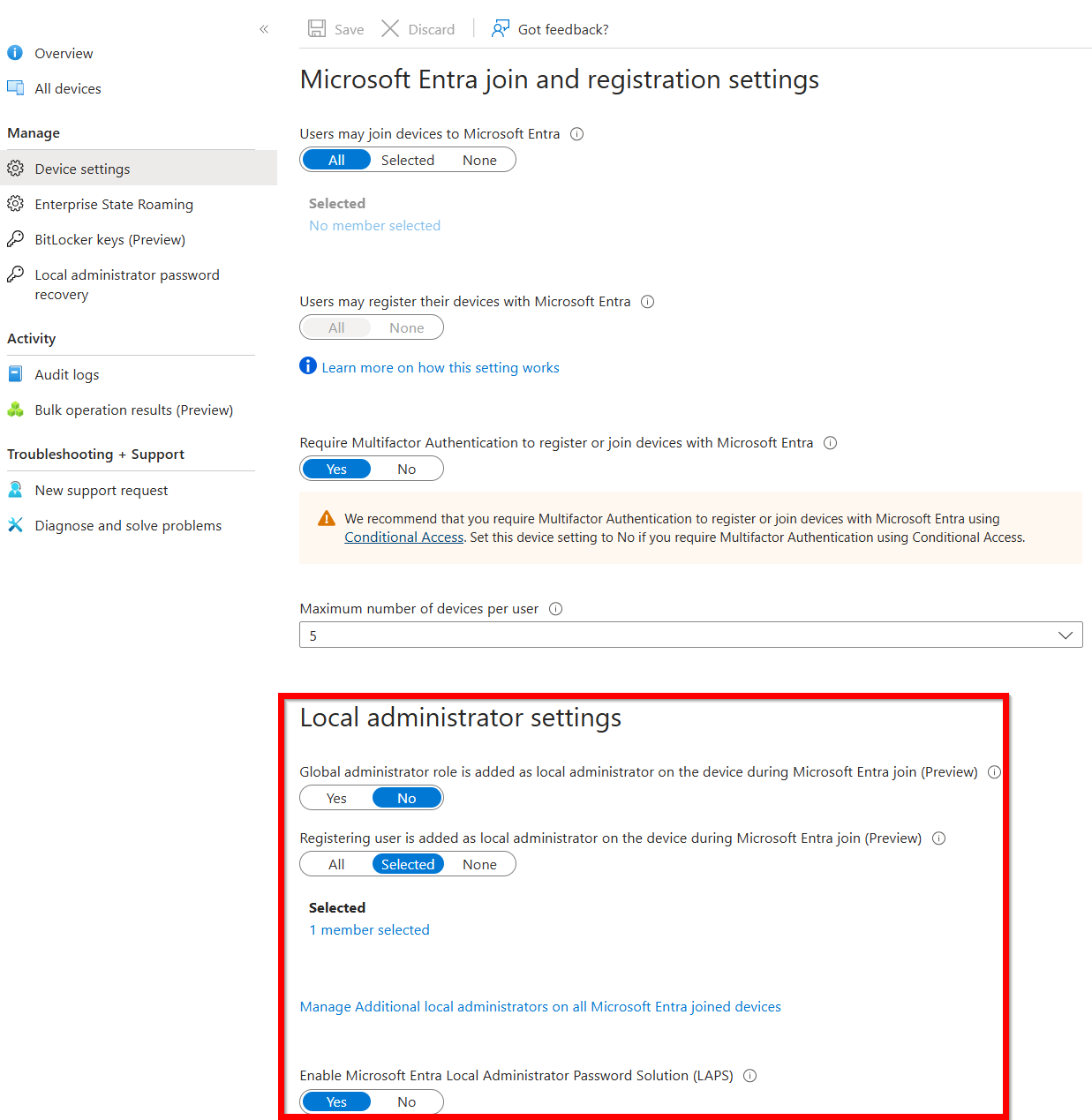
Within Entra ID, we already have a set of controls to narrow down the risk for Entra Joined devices and extend controls we can use later on in Intune.
In the screenshot below, you’ll see we first prevent Global administrators from being Local administrators on all devices by default, which narrows down ‘lateral movement’, I’d say.
Secondly, we scope the registering user to be added to the local administrators group during setup. For this, we use the Win-Usr-LocalAdministator group, as its members are authorized to be local admins—but only on their own devices.
⚠️Note: This setting is only needed when you are joining existing devices to Entra/Intune and for APv2, otherwise you can change this to None.
And of course, we enable LAPS to be set up in Intune later on!
Autopilot
In the setup, I aim to separate device and user configurations. That applies to the Autopilot setup as well. We do configure two profiles, one for the standard user and one for administrators. And of course, we assign the right groups to the right profile Win-Dev-StandardUser and Win-Dev-Administrator.
This creates our first layer of control over who may become a local administrator when the device is being set up.
Intune
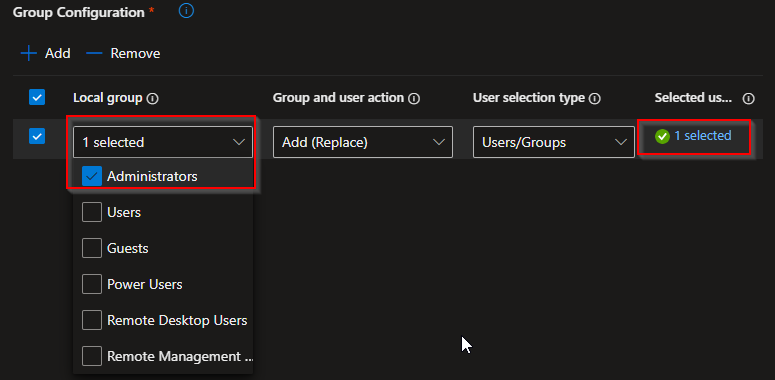
Have you ever heard of Local user group membership? It’s a good way to manage who ends up in the Administrators group on each device.
We will configure the policy Win - Local admins - D - Replace to ensure that, on every device in the Win-Dev-Standarduser group, only the users from Win-Usr-LocalAdministrator-All are added to the Administrators group on the device, and otherwise it’s a placeholder.
⚠️ Tip: It can be confusing, but there’s a difference between Add (Replace) and Add (Add) actions. Be careful when configuring this. Personally, I prefer Replace over Remove, as it gives us more control instead of focusing on removing specific users.
Secondly, we configure the Win - Local admins - D - Add and assign the group Win-Dev-Administrator to it. In the add action, we target the group Win-Usr-LocalAdministrator-All again.
This allows users who need admin access on all devices to be added—without removing the end user.
I know this profile doesn’t fully prevent future misuse (as it doesn't check if others are added), but ideally, these end users will be using EPM.
As of March 2025, the LAPS controls are extended in the settings catalog to randomize the account name, for example. We’ll use these latest settings to make the setup even more secure. I’ll upload the configuration profile to GitHub, but feel free to tailor the LAPS settings to your needs and assign them to all devices.
There’s no need for custom configurations, because with our group setup, the user won’t be removed or overwritten.
⚠️ Note: Do not enable the Passwordless experience setting in the config profiles, otherwise Windows is trying to extend the LAPS user with your domain name.
Closing note
We created a comprehensive solution to keep the best of both worlds, and reducing the risk that the Administrators group gets a wild-west scenario.
By preventing Global administrators from being added, we lower the risk in case one of those accounts is compromised.
If you want to limit this to Autopilot-registered devices only, consider setting the Entra Join option to None.
With the Local User Group Membership setting, we’ve established fine-grained control over group memberships on the device. And as you may have noticed, this profile also allows you to manage other local groups, not just Administrators, providing even more governance options.
The configuration I could export with IntuneManagement, I stored in my GitHub.
Considerations
It’s recommended to disable of the default Administrator through the Config profile settings—especially since the LAPS user is a newly created account. Note that this setting does not remove the default Administrator from the Administrators group automatically.
The Add (Add) action is not the most secure option, as EPM is in this case. But without EPM, this can be a considerable option for your environment.
Also, keep in mind that configuration profiles do not refresh or reapply by default. I strongly recommend enabling Config Refresh within your config profiles (if you haven’t already). My good friend Nicklas made an excellent blog about it!
Is this the most secure solution? No, definitely not.
Is it manageable, does it add control, and bring real value to your environment?
Absolutely.
Thanks for taking the time to read this blog!
Do you have any feedback or adjustments I should make? Please let me know.